一.简述 <font style="color:rgba(0, 0, 0, 0.86);">JEP290</font>过滤传入的序列化数据。
JEP290 <font style="color:rgba(0, 0, 0, 0.86);">是 Java 为了防御反序列化攻击而设置的一种过滤器。</font>( JDK6u141、JDK7u131、JDK 8u121 支持 JEP290 )
前面学了 6 种攻击,JEP290 在 RegistryImpl 中添加过滤方法,所以只对注册中心的攻击有影响。
服务端攻击注册中心这里用了 CC5 加动态代理(因为 bind 绑定的必须是 Remote,需要借助 proxy 动态代理)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 package org.example;
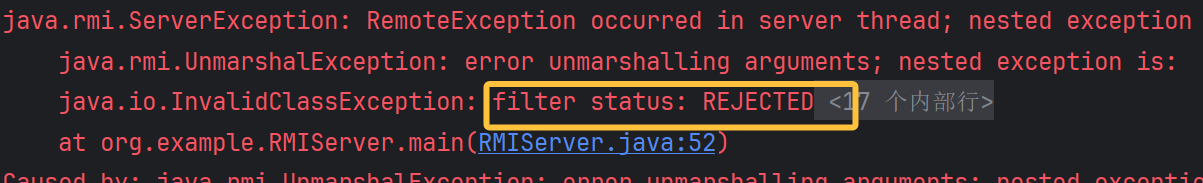
服务端 bind 攻击注册中心,换用 jdk8u131 后继续攻击注册中心会报错:信息: ObjectInputFilter REJECTED: class sun.reflect.annotation.AnnotationInvocationHandler, array length: -1, nRefs: 8, depth: 2, bytes: 284, ex: n/a
bind 绑定的是 proxy 创建的恶意对象,注册中心反序列化的时候就会阻拦
二.过滤分析 报错原因进行分析:
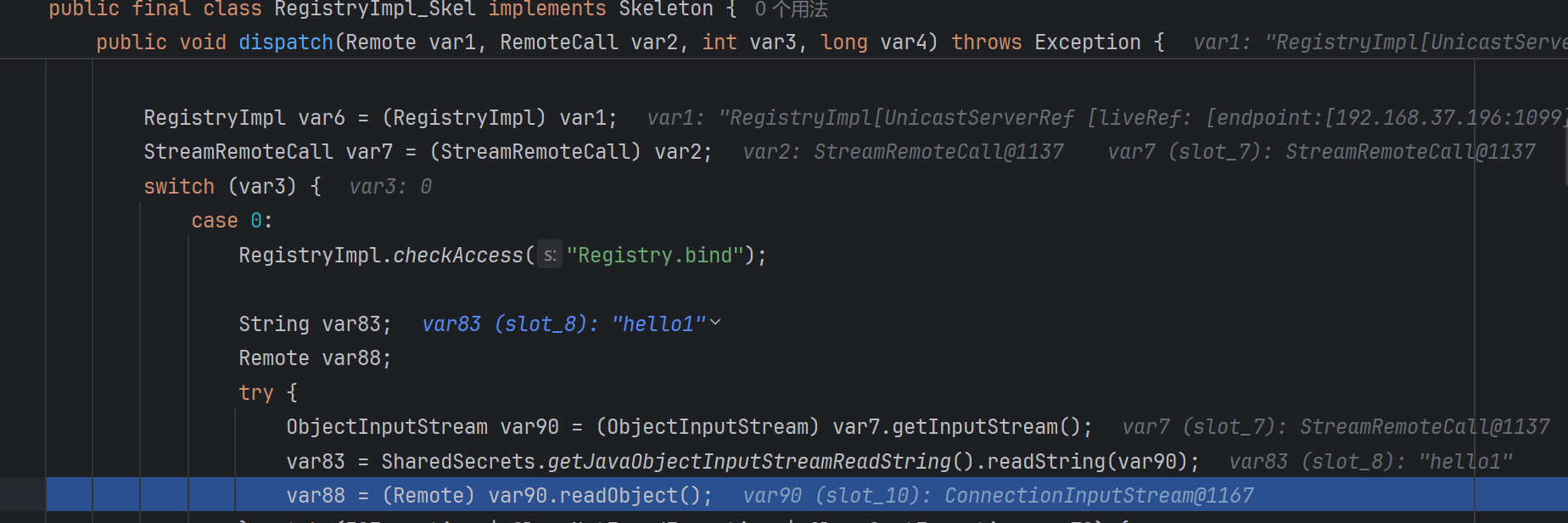
调试看一下,服务端相当于一个客户端给注册中心发起 bind 请求,注册中心 Registry_Skel.dispatch 进行处理
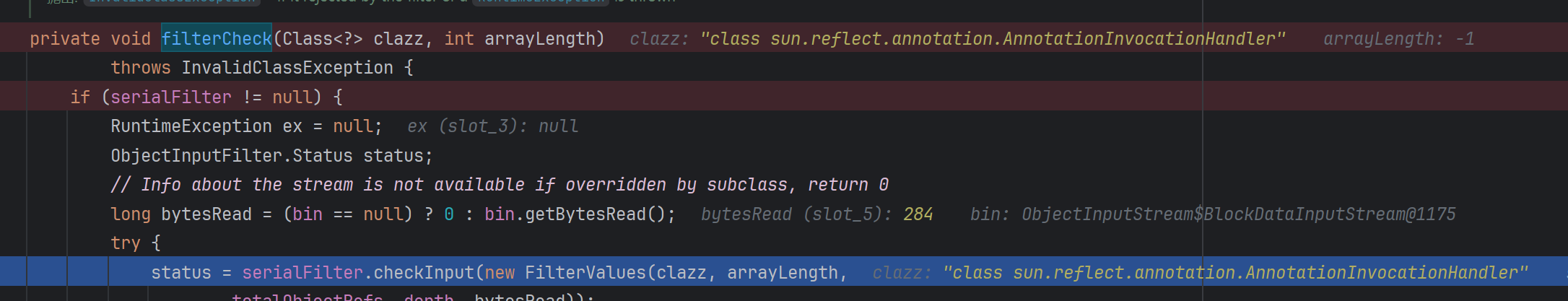
调用 ObjectInputStream.readObject
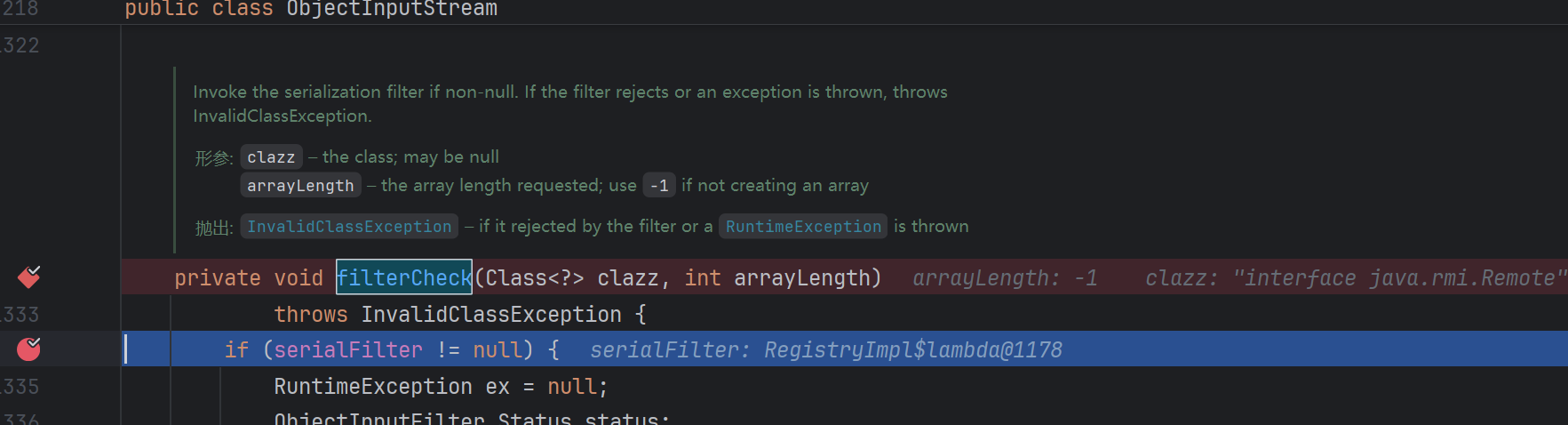
后续跟进发现进到了下的断点方法 ObjectInputStream.filterCheck
后面步入到真正的过滤:RegistryImpl#registryFilter
具体的过滤代码:
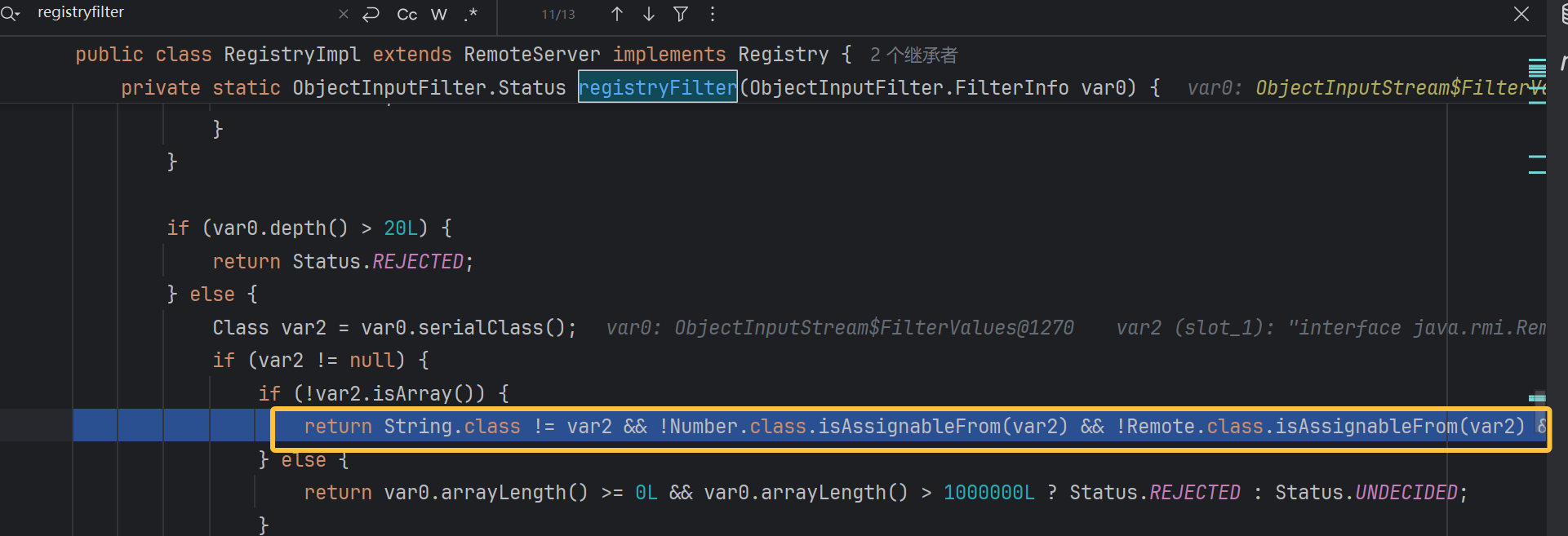
RegistryImpl#registryFilter
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 private static ObjectInputFilter.Status registryFilter(ObjectInputFilter.FilterInfo var0) {
加了白名单限制,不在白名单就会返回 Status.REJECTED :
String.class Number.class Remote.class Proxy.class UnicastRef.class RMIClientSocketFactory.class RMIServerSocketFactory.class ActivationID.class UID.class
这里是一层一层进行检验,最外层是我们用的动态代理创建的 remote,和之后的 Proxy 都在白名单内 status 返回值为 ALLOWED
但到 AnnotationHandler 时会被拦截 status 返回值为 REJECTED 所以报错
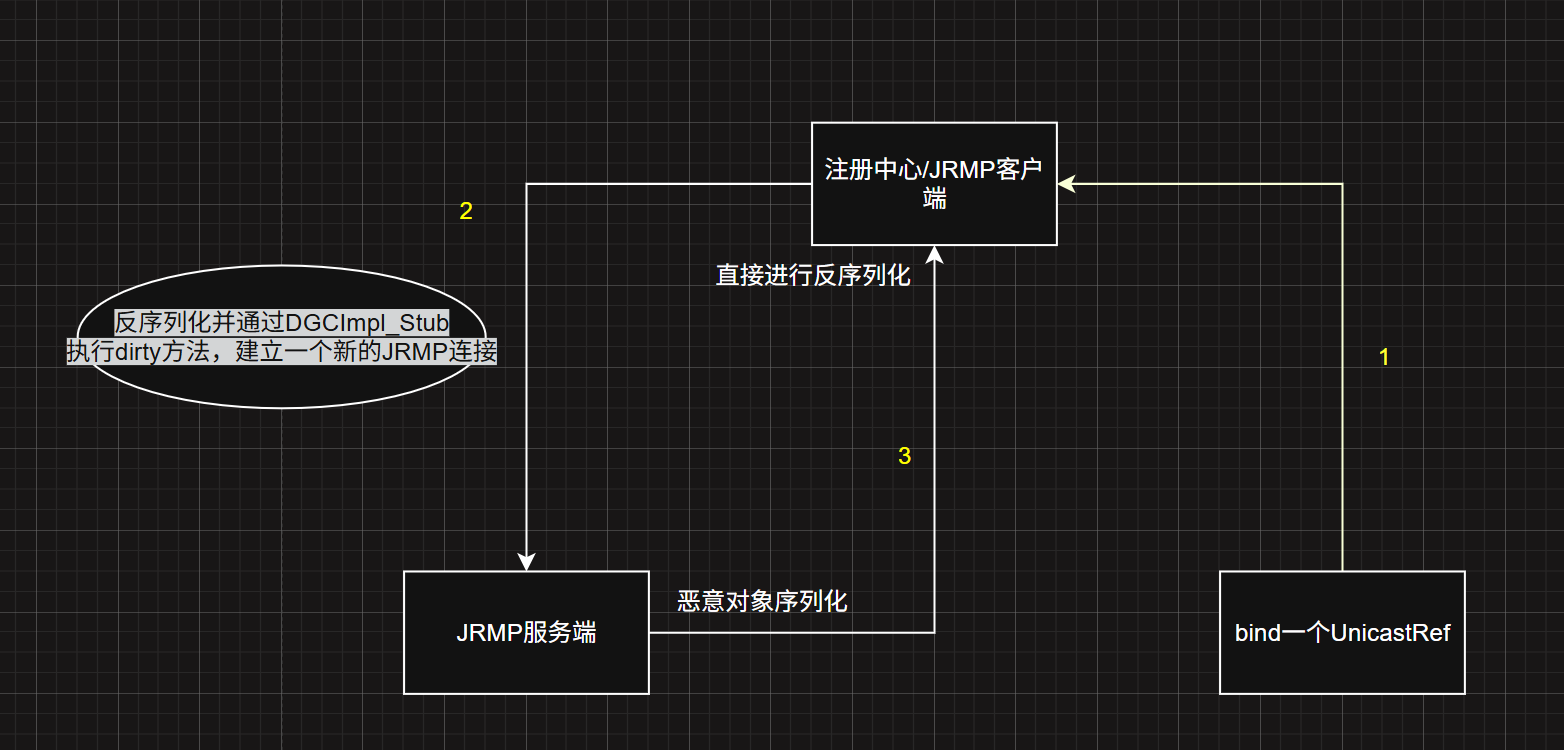
三. 绕过(8u121~8u231) UnicastRef Bypass JEP290(8u121<jdk<8u231)
原理 绕过原理先看总结:
首先用的都是白名单里的类所以 check 都能通过,bind 一个 UnicastRef 的对象
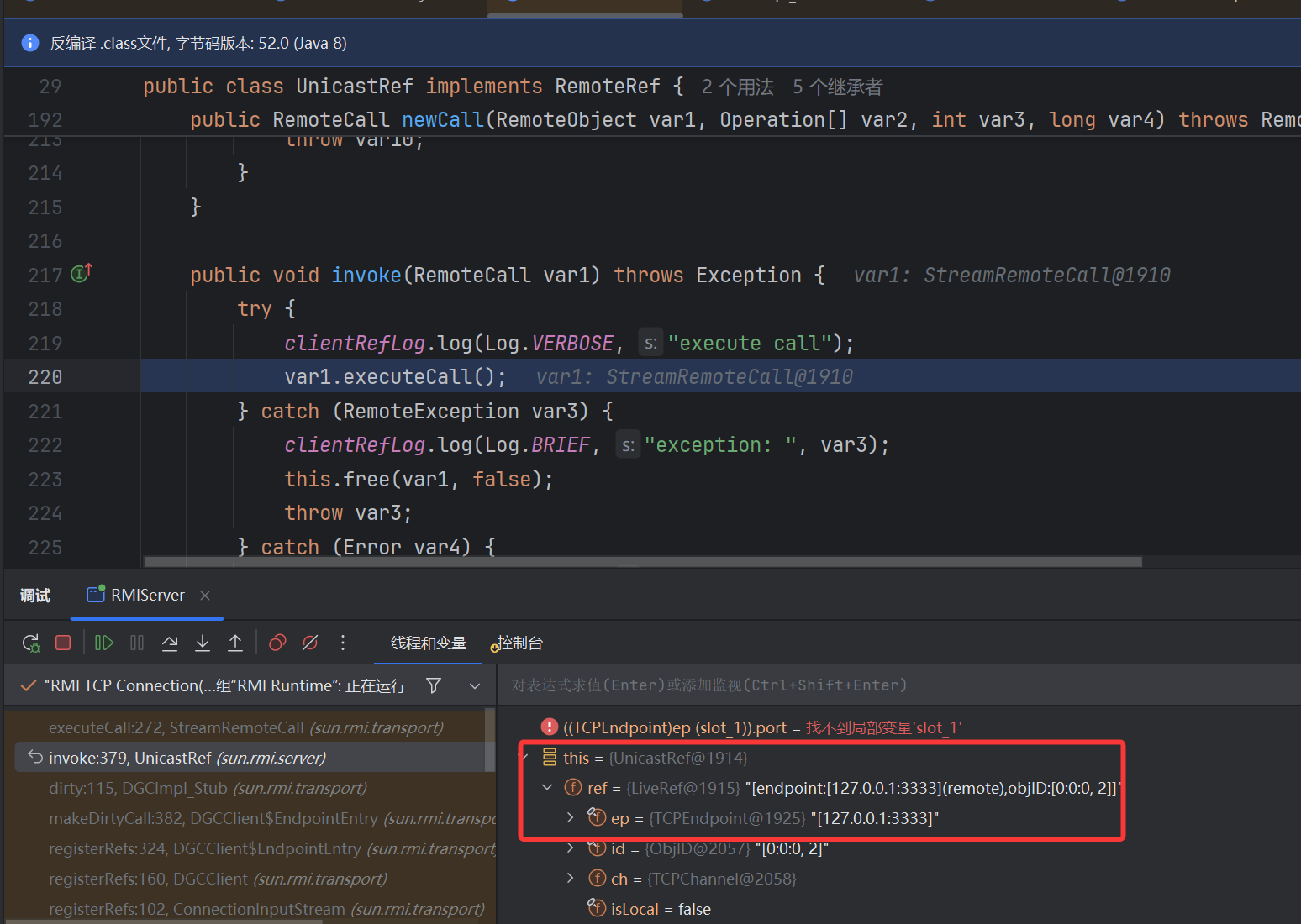
RegistryImpl_Skel 分发处理 bind 进行反序列化,然后会触发 DGC 逻辑 ,就会执行 dirty,向在 UnicastRef 中封装的恶意端发起请求,该过程中底层与之前在 RMI 基础中跟的 DGCImpl_Stub.dirty 一样
该方法里调了 super.ref.newCall ,super.ref.invoke()—>StreamRemoteCall.executeCall 对于返回一定条件会直接反序列化,造成反序列化漏洞
也可以说注册中心反序列化 UnicastRef 之后,它就可以看作一个JRMP 客户端 ,向恶意服务端端发起 dirty 请求建立一个JRMP 连接 到用 ysoserial 开启的 JRMP 服务端,这样就类似于一个服务端攻击客户端了
JEP290 默认只为 RMI 注册表 和 RMI 分布式垃圾收集器 (DGC 层)提供了相应的内置过滤器,但是最底层的 JRMP 是没有做过滤器的。
无论 RMI Registry、RMI Client、RMI Server、DGCClient 的任意两者通信,它们发起 JRMP 请求都利用了 UnicastRef 类。
接着先看反序列化后怎么触发的 DGC 逻辑:
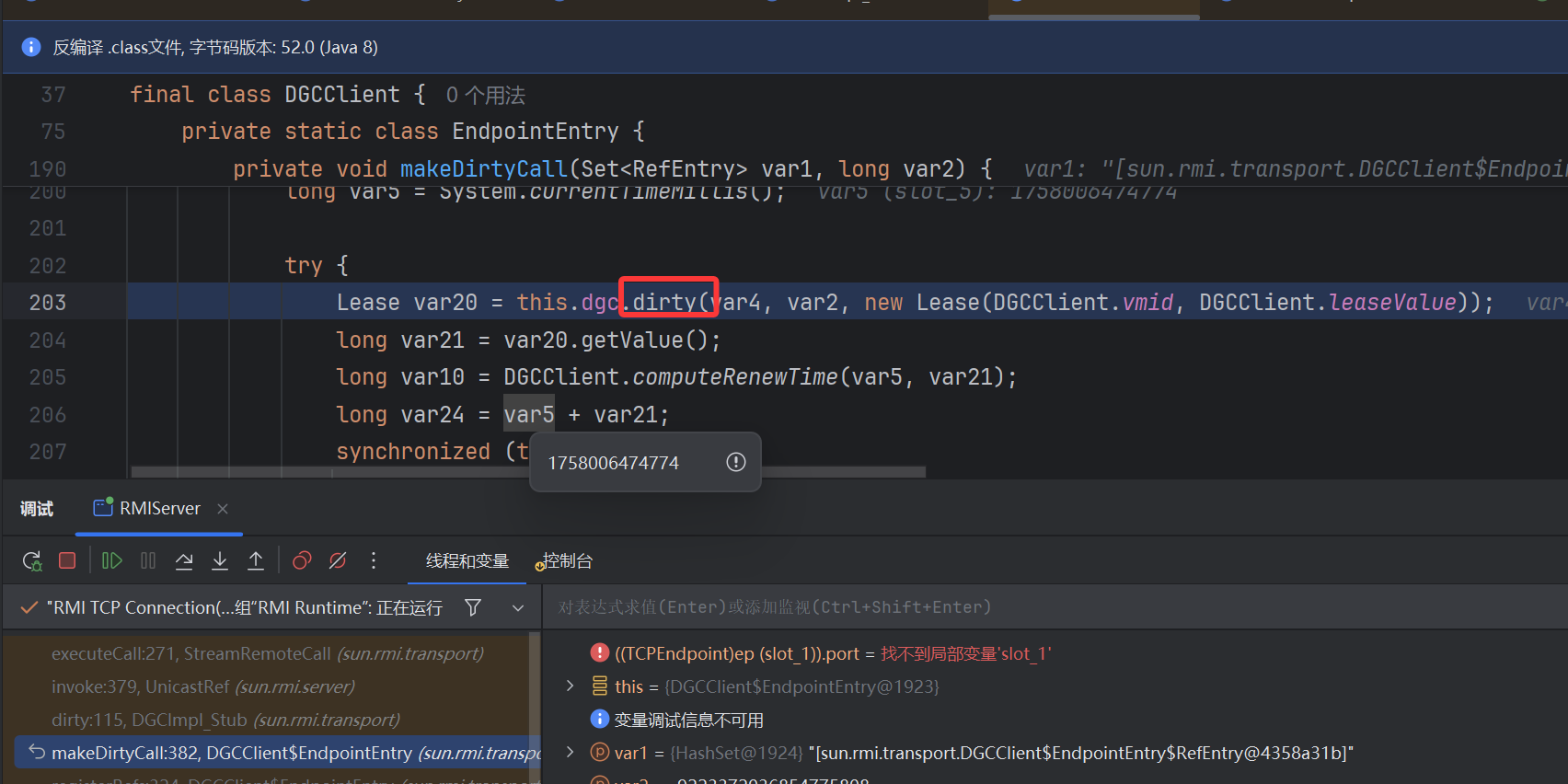
通过白名单 check 后进行反序列化,注册中心 UnicastServerRef.dispatch 分发处理,而存在静态 skel,进而转到 Registry_Skel.dispatch 进行处理反序列化—–>DGCClient.makeDirtyCall 调用 dirty
dirty 里面就到了网络请求这里,可以看到 ref 就是 LiveRef,里面封装了 TCPEndpoint,有我们设置的恶意监听端,触发 JRMP 后将返回结果直接进行反序列化
调用栈:
复现
用 ysoserial 相当于重构了一个 JRMP 服务端,攻击用的是 cc5
运行注册中心
1 2 3 4 5 6 public class RMIServer {
服务端进行操作 bind 绑定 UnicastRef 对象,这里还是借助了动态代理
1 2 3 4 5 6 7 8 9 10 11 12 13 public class RMIServer {
四.另外一种绕过 8u231~8u240
修复点 修复点一:不论哪种方法,注册中心的分发进行反序列化后抛出异常就会消除 ref,就是一个建立新的 JRMP 连接的重要东西
而这里抛出异常时必定的:在反序列化之前进行了类型转换,强制类型的 Object 向下转换会报错 ClassCastException
1 2 var83 = (String)var90.readObject();
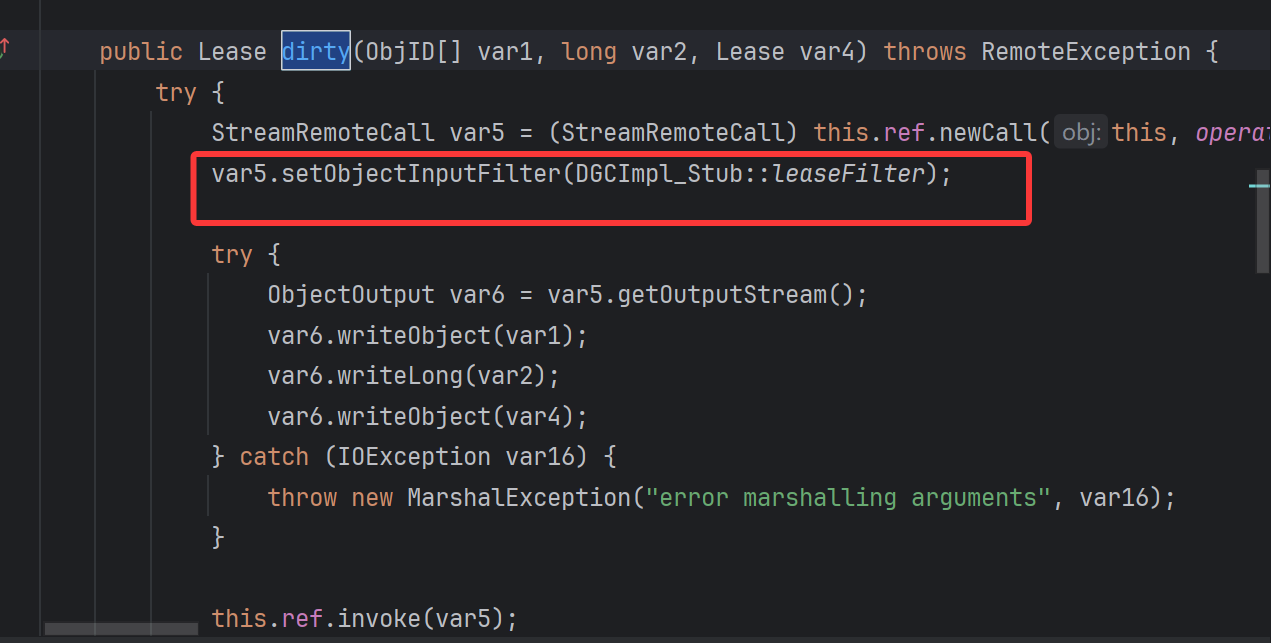
修复点二:一的修复已经是可以的,第二点还在 DGCImpl_Stub#dirty 里面做了修改,在执行 newCall 发起 JRMP 请求之后设置里一个过滤,才进行 ref.invoke 反序列化解析
上面的绕过是 UnicastRef 类包装了一层,通过递归的形式反序列化,再通过 DGCClient 执行 dirty,发起 JRMP 请求 ,现在的绕过是直接在反序列化时就触发 JRMP 请求 ,进入到 UnicastRef.invoke 解析
bind 的或者注册中心 dispatch 分发之后反序列化的是一个远程对象的引用,按照 RMI 基础中的分析来讲注册中心相当于一个客户端反序列化后要会将程对象 exportObject 发布出去该过程中就会建立网络连接
调用链 UnicastRemoteObject.readObjet—>UnicastRemoteObject.reexport 该方法中的 ssf 是在 exp 中设置的
1 2 3 4 5 6 private void readObject(java.io.ObjectInputStream in)
1 2 3 4 5 6 7 8 private void reexport() throws RemoteException
继续是重载的 exportObject—->服务端引用 UnicastServerRef.exportObject
1 2 3 4 5 6 7 8 public static Remote exportObject(Remote obj, int port,
1 2 3 4 5 6 7 8 9 10 private static Remote exportObject(Remote obj, UnicastServerRef sref)
来到 UnicastServerRef.exportObject,这部分和基础中创建注册中心的分析是一样的都是创建 stub,skel
UnicastServerRef.exportObject
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 public Remote exportObject(Remote var1, Object var2, boolean var3) throws RemoteException {
最终调 —–>LiveRef.exportObject—->TCPEndpoint.exportObject——>TCPTransport.exportObject.listen 一系列调用 listen 方法
TCPTransport.exportObject()—>listen()
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 public void exportObject(Target var1) throws RemoteException {
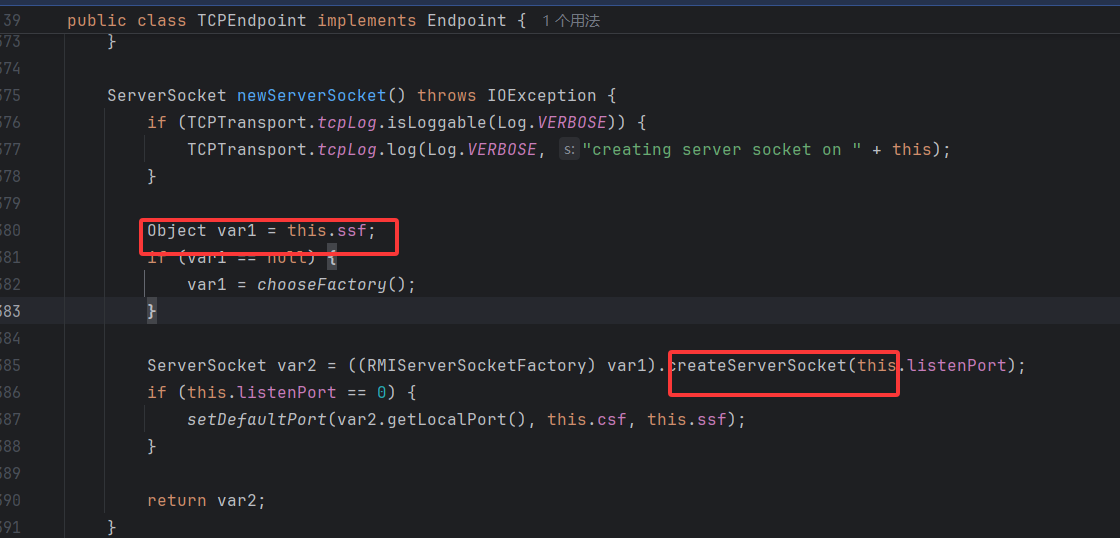
在 listen 中调用了 newServerSocket 方法
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 private void listen() throws RemoteException {
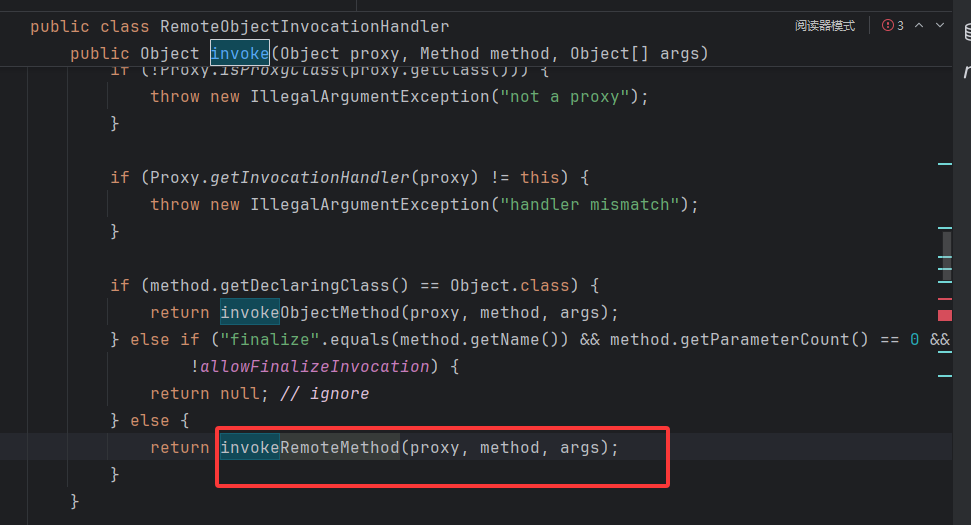
ssf 在 newServerSocket 这里调了一个方法,而它是我们设置的动态代理,在这里调用 RemoteObjectInvocationHandler 调用处理器的 invoke 方法
这里的连接也就是基础中说的从客户端的调用处理器到客户端的引用进行 JRMP 连接
前面的 if 都不满足直接调最后面的 invokeRmoteMethod
这里的 ref 在 payload 中是设置的 UnicastRef
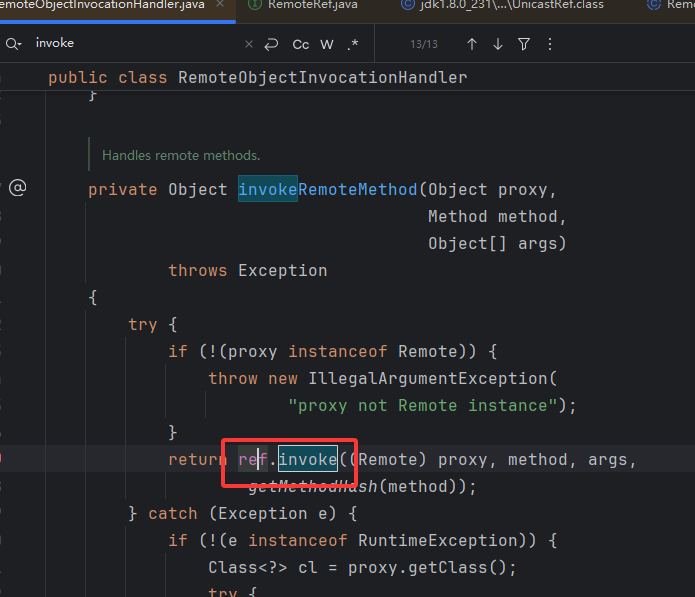
那就来到了客户端发起 JRMP 连接的地方了 UnicastRef.invoke,这里的流程还是和 RMI 基础中的 RMI 类比动态代理一样样,先是客户端代码层面的调用处理器,然后客户端的引用 UnicastRef 建立 JRMP 连接并反序列化返回的数据,服务端就省略了….
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 ......Connection var6 = this .ref.getChannel().newConnection();StreamRemoteCall var46 = new StreamRemoteCall (var6, this .ref.getObjID(), -1 , var4);ObjectOutput var10 = var46.getOutputStream();this .marshalCustomCallData(var10);for (int var12 = 0 ; var12 < ((Object[])var11).length; ++var12) {Class var47 = var2.getReturnType();if (var47 != Void.TYPE) {Object var48 = unmarshalValue(var47, (ObjectInput)var11);return var48;
并且上面获取到的 InputStream 并没有进行设置 JEP290 的过滤,直接反序列化可以 Bypass
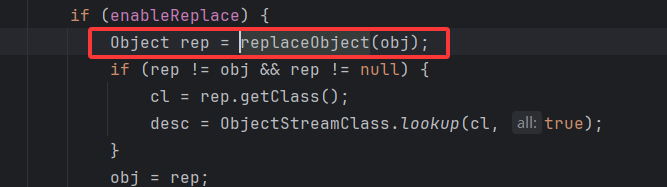
小问题 在本地 bind 或者 rebind 的时候,UnicastRef.invoke 方法中进行反序列化时
enableReplace 默认为 true,会调用MarshalOutputStream#replaceObject
当绑定的对象没有继承 RemoteStub 时,直接就会返回从静态表中获得的 stub,即原先的 UnicastRemoteObject 还会被转换成为 RemoteObjectInvocationHandler,就会导致服务端无法触发 UnicastRemoteObject 反序列化
1 2 3 4 5 6 7 8 9 10 protected final Object replaceObject(Object var1) throws IOException {
所以就得在 payload 中重新写一下 bind 方法,在序列化之前反射修改 enableRepolace 为 false,使他不进行转换
原本的 bind 方法:
1 2 3 4 5 6 7 8 9 10 11 12 RemoteCall var3 = super.ref.newCall(this, operations, 0, 4905912898345647071L);
重写的和之前反序列化攻击里面的一样。。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 static void bindReflection(String name, Object obj, Registry registry) throws Exception {
最终:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 package org.example;
文章 https://m0d9.me/2020/07/11/RMI%EF%BC%9A%E7%BB%95%E8%BF%87JEP290%E2%80%94%E2%80%94%E4%B8%AD/
https://www.anquanke.com/post/id/259059#h2-3
https://cert.360.cn/report/detail?id=add23f0eafd94923a1fa116a76dee0a1
https://xz.aliyun.com/news/8299
https://www.cnblogs.com/tr1ple/p/12335098.html?utm_source=tuicool